Security Tapestry’s SOC Audit: Beyond Compliance
Welcome to Security Tapestry’s SOC Audit—a comprehensive service designed to guide and support organizations through the intricacies of SOC establishment, operation, and regulatory compliance. At the heart of our offering lies a dual-focused approach: not only do we provide meticulous SOC audits to ensure your operations align with industry standards and regulations, but we also offer an unparalleled “Start a SOC” option tailored for businesses venturing into the creation or optimization of their internal security operation center.
From Assessments to Audit Ready Faster Than Ever

Streamline Your Compliance Journey: One Platform for All Your Data
Unify the gathering and safeguarding of all your compliance and audit information on a single, secure, and efficient platform. This ensures that every piece of data you need is right at your fingertips, making your compliance process as smooth as possible.
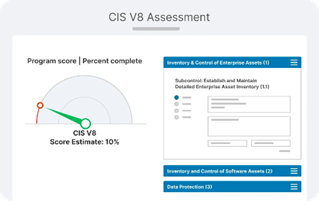
Synchronize Your Team Effortlessly
Facilitate flawless communication by sharing important updates with auditors and delegating tasks to team members effortlessly. Our platform is designed to keep your audit process organized and everyone aligned, enhancing collaboration and efficiency.
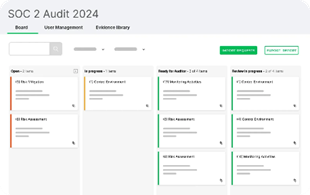
Enhance Transparency and Oversight
Monitor your audit’s progress in real-time with our intuitive Kanban-style dashboard, tailored to provide distinct perspectives for auditors and your internal team. This feature is designed to offer comprehensive visibility, allowing for better planning and decision-making.
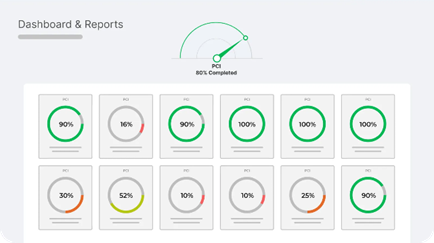
Comprehensive Support at Your Fingertips
Our dedicated cybersecurity professionals are here to assist you every step of the way. From conducting quarterly reviews to offering expert audit advice, we’re committed to ensuring your compliance journey is supported by knowledge and expertise, giving you peace of mind.
How It Works
Established and Robust Cybersecurity Programs
Regulatory Compliance and Comprehensive Support:
Our SOC Audit service transcends traditional boundaries by not just evaluating your current SOC maturity against regulatory requirements but also by offering detailed guidance and strategic direction to bridge any gaps identified during the audit process. This ensures that your organization is not only compliant but also equipped with a robust and proactive defense mechanism against cyber threats.
Less Established Cybersecurity Programs
Start a SOC – Your Pathway to Cyber Resilience:
Recognizing the challenges and complexities involved in establishing an internal SOC, we offer end-to-end support that covers everything from foundational planning to operational execution. Whether you’re at the conceptual stage or partway through SOC development, our experts are here to accelerate your journey towards achieving a fully functional, efficient, and compliant SOC. Upon completion, we conduct a comprehensive audit to validate your readiness and compliance, marking your achievement and readiness to face cybersecurity challenges head-on.
With Security Tapestry’s SOC Audit, stepping into the realm of advanced cybersecurity operations and compliance is seamless and straightforward. Let us guide you from start to finish, ensuring your organization stands resilient in the face of evolving cyber threats.
Tailored Approaches for Every Stage of Your SOC Journey
Security Tapestry’s SOC Audit service is designed to meet organizations at any stage in their Security Operations Center (SOC) lifecycle. Whether you’re looking to build a SOC from the ground up, enhance an existing setup, or validate a fully operational center through a comprehensive audit, our approach is tailored to fit your specific needs. Here’s how we support you across these scenarios:
1. Starting a New SOC
- Step 1: Initial Consultation and Planning
- We begin with a deep dive into your organization’s current cybersecurity posture and objectives. This phase involves understanding your specific needs, the scope of your cybersecurity goals, and the regulatory standards you aim to meet.
- ________________________________
- Step 2: Design and Implementation
- Based on the initial consultation, we design a SOC strategy that includes infrastructure setup, technology selection, and process development. Our team of experts will guide you through the implementation process, ensuring that every aspect of your SOC is optimized for efficiency and effectiveness.
- ________________________________
- Step 3: Training and Staffing
- To ensure your SOC operates smoothly, we provide comprehensive training for your staff, covering operational procedures, incident response, and best practices in cybersecurity. We also offer guidance on staffing, helping you build a skilled team that can manage your SOC effectively.
- ________________________________
- Step 4: Audit and Compliance Verification
- Once your SOC is up and running, we conduct a thorough audit to assess its alignment with regulatory requirements and industry best practices. This final step ensures that your new SOC is not only operational but also fully compliant and ready to meet real cybersecurity challenges.
2. Enhancing an Existing SOC
- Step 1: Assessment and Gap Analysis
- For SOCs that are partially established but need further development, we start with an exhaustive assessment of your current setup. This involves identifying any gaps in technology, processes, or skills that could hinder your SOC’s effectiveness.
- ________________________________
- Step 2: Customized Improvement Plan
- Based on the assessment, we develop a customized plan to address the identified gaps. This could involve integrating new technologies, refining operational processes, or enhancing staff training and development.
- ________________________________
- Step 3: Implementation and Optimization
- With the improvement plan in place, our experts support you through the implementation of recommended changes, ensuring that your SOC evolves to meet both current and future cybersecurity needs.
- ________________________________
- Step 4: Final Audit for Compliance and Efficiency
- After enhancements are implemented, we conduct a comprehensive audit to validate improvements and ensure your SOC meets all necessary compliance standards and operational benchmarks, marking a significant milestone in your SOC’s development journey.
3. Auditing a Fully Operational SOC
- Step 1: Comprehensive SOC Audit
- For fully operational SOCs, our focus is on conducting a detailed audit that evaluates your SOC’s compliance with relevant regulations and its effectiveness in managing cybersecurity threats. This involves a thorough review of processes, technologies, and staff competencies.
- ________________________________
- Step 2: Detailed Report and Recommendations
- Upon completing the audit, we provide a detailed report that outlines your SOC’s current state, highlighting strengths and identifying any areas for improvement. We also offer actionable recommendations to ensure continuous improvement and compliance.
- ________________________________
- Step 3: Support for Implementation of Recommendations
- Should any improvements be needed, our team is ready to assist in implementing these recommendations to ensure that your SOC not only maintains compliance but also operates at the pinnacle of cybersecurity defense effectiveness.
What Our Customers Say
“As a Compliance Officer, finding a solution that consolidates all our audit and compliance data in one place seemed like a tall order until we discovered this platform. Not only has it streamlined our data management, but it has also enhanced team coordination immensely. Sharing updates and delegating tasks has never been smoother, and the level of transparency and oversight we now have is unparalleled. Our audit process is more organized and efficient, thanks to this comprehensive platform. It’s truly transformed our approach to compliance.”
Security Tapestry Operations Warranty
Your Security, Our Commitment
Embrace the peace of mind with Security Tapestry’s Operations Warranty. When you become a customer, you’re backed by our cybersecurity warranty. This includes up to $1,000,000 in financial assistance to address cybersecurity incidents, ensuring you’re supported not just in defense, but also in recovery and resilience.
Ready to enhance your cybersecurity strategy?
Connect with us today to set up an initial conversation with our Security Tapestry experts. Discover how our tailored security solutions can make a difference for your organization.
